| MCP (Model Context Protocol) is a rapidly adopted open standard that lets AI agents securely and consistently access company data, tools, and workflows. Properly designed and governed, MCP can reduce operating costs in pharmaceutical manufacturing by automating routine tasks, accelerating decision-making, and minimizing rework, while maintaining GMP (Good Manufacturing Practice) compliance. However, the cost benefits are not automatic: they depend on careful design (data lineage, identity & access controls, validation), risk controls for MCP endpoints, and changes to SOPs and validation approaches. Recent industry write-ups and pilots demonstrate strong productivity upside, growing vendor support (including major platform vendors), and emerging security concerns that need to be addressed before scale deployment. |
Introduction, why this matters for pharma manufacturing
Pharma manufacturing sits at the intersection of two demanding constraints: the need for tight regulatory control (GMP, traceability, audit readiness) and the need for operational efficiency (lower cost per batch, less downtime, faster release). AI agents promise productivity gains, faster batch reviews, automated deviation triage, dynamic SOP assistance, and predictive maintenance, but until recently, integrating models with an organization’s ERP, LIMS, DMS, and MES has been custom, fragile, and expensive.
The Model Context Protocol (MCP) changes that. MCP creates a standard connector between LLM-based agents and enterprise services, so AI can request relevant context, call approved tools, or run workflows using a stable, auditable interface. For life sciences teams, this means the possibility of safely automating repeatable knowledge work while keeping audit trails intact, if done correctly.
This article explains:
- What MCP is and how it maps to GMP-relevant processes.
- Where real cost savings come from.
- How MCP can be deployed without undermining compliance.
- The security and validation pitfalls to avoid.
- A practical implementation roadmap and measurable KPIs.
- An illustrative cost vs. compliance-risk model (figure included).
What is CP (succinct, plain language)
- Definition: MCP is an open protocol that standardizes how AI models connect to tools and data sources. Think of it as a “USB-C” for AI agents: one standard interface that multiple models and services can use.
- How it works (simple): An MCP server exposes named resources (documents, database queries, calculators, and workflows). An AI agent requests a resource, the MCP server enforces access rules, and the agent acts on the returned context or triggers a workflow.
- Why useful: It reduces custom integration work, improves reuse, and enables consistent governance across many agents and models.
Note: MCP is distinct from the older, domain-specific “Manufacturing Control Plan” (same acronym). In this article MCP = Model Context Protocol (AI connector).
How MCP maps to GMP-relevant functions in pharma manufacturing
MCP can be applied to many GMP workflows. Examples:
- Batch record review & release: the agent fetches the validated batch record, run logs, LIMS results, and deviation history via MCP; it prepares a draft checklist and highlights out-of-spec or missing items for QA review.
- Deviation triage & CAPA suggestion: the agent queries historical deviations, finds similar events and their root causes, and suggests corrective/preventive actions for human review.
- SOP assistance & training: Agents with MCP access can present the exact SOP sections relevant to an operator’s task, show change history, and confirm the most recent approved version.
- Change control screening: the agent pulls the change record, impacted systems, and suggested validation scope to prepare a preliminary risk assessment.
- Predictive maintenance & scheduling: the agent consumes MES and equipment telemetry via MCP, flags anomalies, and proposes maintenance windows that minimize batch impact.
- Regulatory intelligence: the agent queries consolidated regulatory databases and the company’s validated product master files to surface inspection-relevant risks.
Each of the above keeps the human-in-the-loop for decisions that require judgment, while the agent handles repetitive retrieval, cross-referencing, and early filtering, the typical sources of cost and delay.
Where the cost savings come from (concrete mechanisms)
Pharma manufacturers can realize savings across three buckets:
- Labor efficiency (desk-based tasks):
- Time saved for QA reviewers, release engineers, and documentation teams by automating initial reviews, checklists, and cross-references.
- Example mechanisms: automated batch review pre-checks, auto-drafts for CAPA, and auto-filled forms that reduce manual data copying.
- Cycle-time reduction (throughput improvements):
- Faster release and shorter hold times lower inventory carrying costs and reduce lost production windows.
- Example mechanisms: faster root cause hypothesis generation, quicker decision support for deviations, and optimized maintenance windows.
- Waste and rework reduction:
- Earlier detection of process drift and improved SPC (statistical process control) triggers reduce rejected batches and reprocessing.
- Example mechanisms: MCP-enabled agents that correlate sensor trends with lab results and flag issues before full batch completion.
Illustrative industry numbers: consulting and vendor write-ups highlight potential double-digit productivity gains in administrative aspects of pharma operations when AI agents are integrated effectively. BCG and industry pilots describe faster agent deployment and meaningful productivity uplift when MCP is used to standardize integrations.
Important: these gains are typically concentrated in knowledge-heavy steps (QA batch review, documentation, deviation analysis). Direct savings in raw materials are usually smaller unless predictive control is implemented end-to-end.
Can MCP preserve GMP compliance? — Short answer: yes, if you design governance and validation into the deployment
MCP itself is a connector. Whether compliance is preserved depends on how you control the connector and integrate it into validated systems.
Key compliance controls to implement:
- Authentication & identity management: no static tokens. Use ephemeral credentials, just-in-time access, and centralized identity linking humans, machines, and AI identities. This prevents “identity fragmentation” attacks and reduces the chance that an MCP endpoint acts with unauthorized privileges.
- Access scoping & least privilege: MCP endpoints should only expose the exact resources an agent needs. Implement role-based access controls and context-aware approvals.
- Auditability: every MCP interaction must generate an auditable record (who/what requested what, when, response fingerprint). Logs should be append-only, retained per policy, and integrated into existing electronic records.
- Data lineage and provenance: when an agent returns a finding, it must also provide provenance metadata (source document IDs, versions, timestamps), so humans can trace and verify statements.
- Change control & validation: treat MCP connectors and agent logic as regulated system components. Define validation requirements (IQ/OQ/PQ equivalents for the agent’s role), acceptance criteria, and revalidation triggers (model updates, schema changes).
- Operator SOP updates & training: update SOPs to reflect agent usage, responsibilities, and fallback procedures if the agent is unavailable or gives uncertain guidance.
- Human-in-the-loop gating: critical decisions (release, safety deviations, regulatory submissions) must remain under human control. Agents should provide recommended actions, not unreviewed changes to the master systems.
With these controls, MCP becomes an audit-friendly integration layer rather than a compliance threat. Several industry guides and vendor posts have started to document recommended patterns for secure MCP deployments in manufacturing contexts.
The security caveat: identity fragmentation & token risk
Security researchers and coverage show a central risk: MCP broadens the reach of agents into enterprise systems, which is powerful and dangerous if identity and access are fragmented.
- Identity fragmentation (multiple unmanaged machine identities and stale tokens) can enable lateral movement by a compromised agent or developer machine. Industry coverage warns that without consolidated identity management, attackers can exploit static credentials or misconfigured MCP endpoints.
- Mitigations: unified identity platforms, ephemeral credentials, centralized secrets management, and strong observability. Microsoft and others implementing MCP support are building registry-level controls and user consent prompts to limit exposure.
From a GMP perspective, security controls are compliance controls: a data breach or uncontrolled changes are not just security incidents, they are regulatory events. So secure MCP is mandatory, not optional.
Validation strategy and documentation (GxP practicalities)
When an MCP-enabled agent touches GMP systems, apply regulated-system validation principles:
- Classification: define the agent/MCP function as either part of the GxP system (e.g., automated release decision) or a non-regulated assistive tool (e.g., draft generation). Higher classification → stricter controls.
- Requirements traceability: write user requirements that specify permitted data sources, response formats, and acceptance criteria.
- Test plans (IQ/OQ/PQ-like):
- IQ: verify the MCP server and agents are installed/configured per design.
- OQ: test access controls, provenance metadata, and error handling.
- PQ: run realistic scenarios (batch review, deviation triage) and confirm acceptable outcomes and operator workflows.
- Change control: establish triggers for revalidation: model architecture changes, MCP protocol upgrades, or any change to exposed endpoints.
- Documentation: include architecture diagrams, data flow maps, identity maps, test evidence, and SOP updates in the validation pack.
- Periodic review: schedule audits of agent outputs vs human decisions to detect drift and latent errors.
By formalizing this, MCP deployments fit into existing GxP governance rather than bypassing it.
Implementation roadmap (practical, phased)
A conservative, compliance-first rollout reduces risk and helps measure ROI.
Phase 0 — Foundations
- Inventory the systems (LIMS, MES, DMS, ERP) and classify data sources for regulated use.
- Establish unified identity and secrets management.
- Pilot an MCP server in a non-production network.
Phase 1 — Safe pilots (low-risk use-cases)
- Start with non-decision, high-value tasks: SOP search, document summarization, and training assistance.
- Implement full logging and provenance capture.
- Validate agent outputs against manual work for a defined sample size.
Phase 2 — Assisted decision (human-in-loop)
- Move to draft generation for batch review and deviation triage, with QA sign-off required for any action.
- Measure time saved per review, reduction in back-and-forth, and operator satisfaction.
Phase 3 — Controlled automation
- Automate low-risk approvals (e.g., administrative sign-offs) with audits.
- Expand to predictive maintenance and SPC alerting, integrating with maintenance scheduling.
Phase 4 — Scale & continuous monitoring
- Harden the MCP registry, rotate keys, and automate compliance checks for agent outputs.
- Implement ongoing model monitoring, drift detection, and scheduled retraining or model gating.
Measurable KPIs to track ROI and compliance
Track both efficiency and compliance metrics:
Efficiency KPIs
- Time spent on batch release per event (hours → target % reduction).
- Time to close deviations/CAPAs.
- Number of manual data transfers eliminated.
- Percentage reduction in batch hold days.
Compliance KPIs
- % of agent-assisted outputs requiring human correction.
- Incidents related to MCP endpoints (security events).
- Timeliness and completeness of provenance records.
- Audit finding counts related to processes covered by MCP.
Tie financial metrics (labor cost savings, inventory carrying cost reduction) to operational KPIs to compute ROI. Use pilot results to refine assumptions before wide rollout.
Illustrative model & figure
I created an illustrative chart showing how estimated cost savings might increase with the MCP adoption stage, while the compliance risk score declines if governance is well implemented. The numbers are hypothetical and intended to explain the relationship; real results will vary by site and scope.
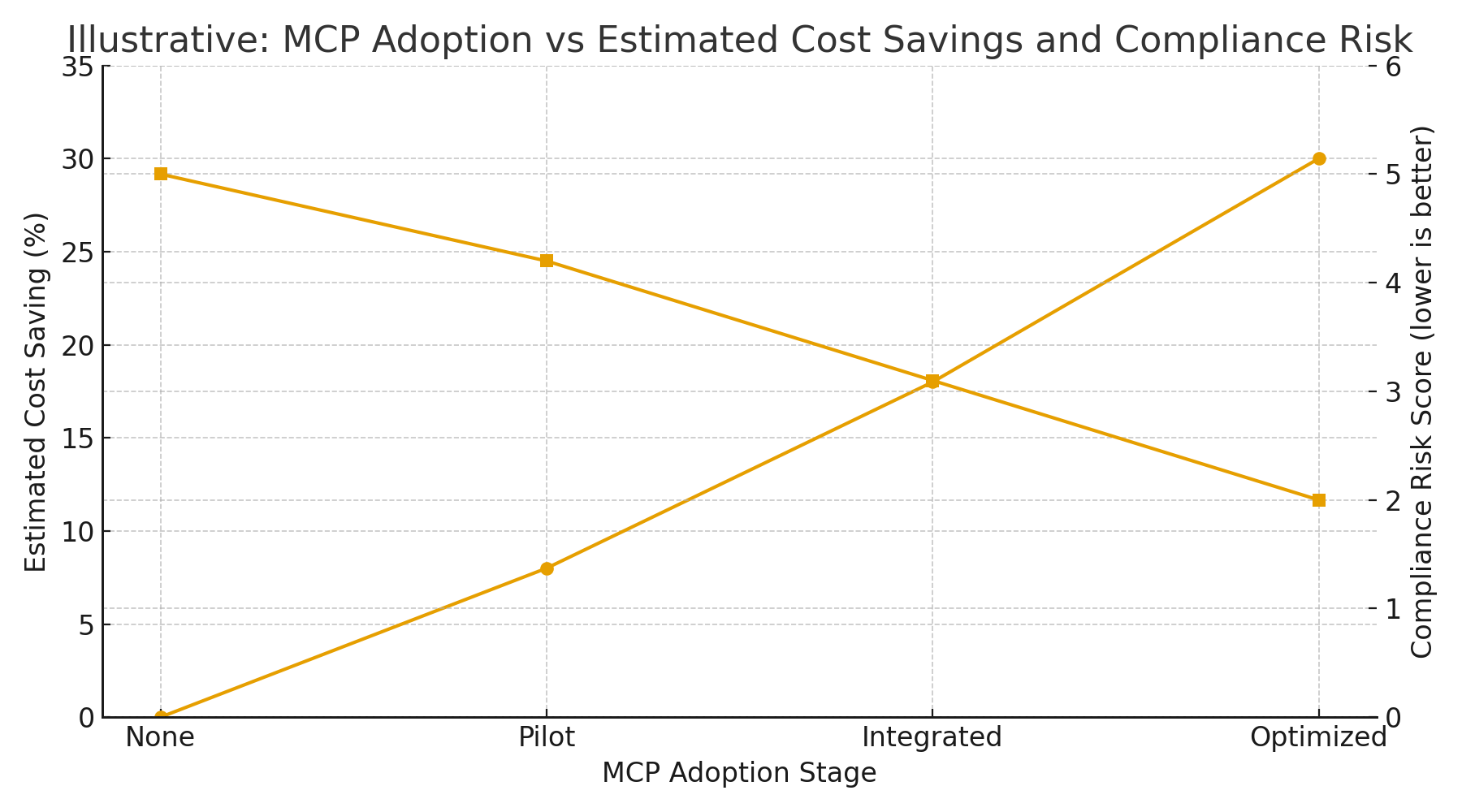
This visual represents the common pattern:
- Small pilot → modest cost savings.
- Integrated, validated deployment with governance → larger savings and reduced compliance risk.
- Optimized deployments that combine MCP with SPC, predictive maintenance, and validated automation → highest savings while keeping risk low.
(Again: figure is illustrative, modelled to aid planning — not empirical field data.)
Current adoption & vendor momentum (industry evidence)
- MCP was introduced as an open-source connector and has been widely covered as a standard that reduces integration costs for AI agents; Anthropic’s work spurred quick adoption and vendor interest.
- Major platform vendors (notably Microsoft) have announced MCP support in platform components to enable richer OS-level AI interactions; this shows the protocol is moving from research into mainstream infrastructure, which matters for enterprise adoption.
- Consulting and industry write-ups (BCG and manufacturing vendors) describe MCP as enabling faster agent deployment and highlighting productivity gains when teams standardize on MCP for factory and enterprise integrations.
- Security reporting flags identity fragmentation as a top risk that must be controlled in any scaled MCP deployment; this is not theoretical, analyst coverage recommends unified identity and ephemeral authentication as primary mitigations.
These signals indicate both opportunity and new areas of responsibility for regulated companies.
Practical SOP language snippets (for SOP authors)
Below are concise, plain-language snippets you can adapt into your SOPs:
SOP excerpt — MCP Access & Use
- “Only authorized users and registered agents may request data via MCP. Each MCP request must include the user or agent identity and a purpose-of-use code. All MCP responses must include provenance metadata (document ID, version, timestamp).”
SOP excerpt — Human-in-Loop Decisioning
- “AI-generated recommendations are advisory only. Final decisions on batch release, quality deviation closure, and change implementation require an authorized human signature. Records of AI recommendations and human decisions will be retained per Records Retention Policy X.”
SOP excerpt — Incident & Change Control
- “Any security incident involving MCP endpoints will trigger immediate containment per Incident Response Plan Y, and a change control assessment to determine the need for revalidation.”
Common implementation mistakes to avoid
- Treating MCP as a black box: Not defining input/output contracts and provenance makes validation impossible.
- Skipping identity consolidation: Leaving machine identities unmanaged amplifies breach risk.
- Allowing agents direct write access to authoritative systems without approvals: Always require human approvals for critical writes.
- Underestimating change-control needs: Model updates and endpoint changes must be part of the controlled change process.
- Over-automating too soon: Automating high-risk decisions without adequate PQ testing invites regulatory problems.
Cost vs compliance: realistic expectations
- Short term (6–12 months): Expect modest cost reductions (single-digit percentage in administrative labor) from pilots that automate search, drafting, and cross-referencing tasks.
- Medium term (12–24 months): With validated integrations and expanded use-cases (deviations, SOP assist), double-digit efficiency gains in documentation and QA throughput are achievable.
- Long term (24+ months): When predictive controls, MES integration, and SPC automation mature, larger cost savings in scrap reduction and throughput can be realized, but these require significant engineering and validation effort.
These timelines assume a thoughtful, compliance-first approach rather than a rapid, ungoverned adoption.
Final checklist for an MCP pilot that aims to reduce cost while keeping GMP intact
- Inventory data sources and classify them for regulated use.
- Establish unified identity and ephemeral credentials.
- Deploy the MCP server in a segmented network; enable full logging.
- Choose a low-risk, high-value pilot (SOP lookup, batch pre-check).
- Define acceptance criteria and measurement plan.
- Implement provenance metadata in responses.
- Run IQ/OQ/PQ-style tests and document results.
- Update SOPs and train staff.
- Scale only after meeting KPIs and security benchmarks.
Conclusion
MCP offers pharma manufacturers a practical path to deploy AI agents safely and at scale. The cost benefits are real, mostly in knowledge work, cycle time, and defect prevention, but they are unlocked only when MCP deployments are governed as part of the regulated system landscape: strong identity, scoped access, provenance, validation, and human gating. With the right design and monitoring, MCP can reduce costs while preserving and even strengthening GMP compliance.
Most frequently asked questions related to the subject.
- Q: Is MCP itself a regulated system?
A: MCP is a protocol/connector. Whether it’s treated as a regulated system depends on the role it plays. If MCP endpoints are used in decision-making that affects product quality (e.g., automated release), treat them as part of the GxP system and validate accordingly. - Q: Can an MCP agent ever be allowed to write directly to a validated system?
A: Technically yes, but only under strict controls: pre-approved write scopes, audit trails, human approvals for critical transactions, and validation evidence that writes behave correctly. - Q: What are the fastest wins for cost reduction?
A: SOP/document retrieval, batch pre-check automation, and deviation triage. These are high-value, lowest-risk starting points. - Q: How do we prove to auditors that an agent’s output is trustworthy?
A: Capture provenance, store agent inputs and outputs, include test evidence showing agent recommendations match expected outcomes, and demonstrate human oversight in critical steps. - Q: What’s the single biggest security control to implement first?
A: Unified identity / ephemeral credentials to prevent identity fragmentation and stolen tokens from being abused.